Project Status: Internal Prototype / Security Research
The most valuable people on the internet—founders, VCs, and security researchers—have a problem.
They are drowning in noise. Their DMs are spammed with “Hi,” “Can I pick your brain?”, and automated sales pitches. To survive, they close their DMs.
But this creates a new problem:
The Signal cannot get through.
If I find a critical vulnerability in a founder’s app, or if I have a high-value confidential offer, I have no way to reach them.
Public mentions get ignored. Emails get filtered. The front door is locked.
So, I built a secure back channel.
Introducing ZeroTrace
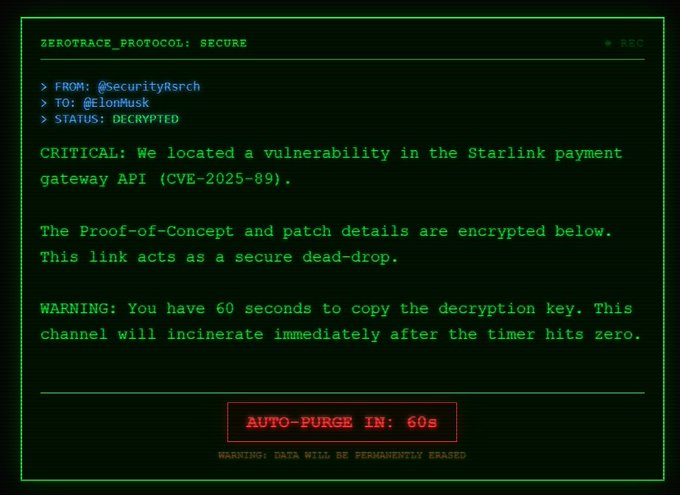
ZeroTrace is a digital dead-drop. It allows you to generate a secure, encrypted uplink to any Twitter/X user, locked specifically to their identity.
It’s not just a messaging app. It’s a protocol with an aggressive promise:
| Property | Description |
|---|---|
| Identity Locked | Only the verified owner of the target handle can open it. |
| Zero Knowledge | The server decrypts the payload once. |
| Burn After Reading | 60 seconds after access, the data is destroyed forever. |
The Interface
How It Works (The Protocol)
I wanted the experience to feel less like “sending an email” and more like sliding a classified briefcase across the table.
1. The Uplink (Encryption)
- Message drafted in the browser
- Sent to Django backend
- Encrypted via Fernet symmetric encryption
- A unique
uuidgenerated - Key stored temporarily
- Payload locked to a specific Twitter/X ID (e.g.,
@ElonMusk)
2. The Handshake (Authentication)
- Recipient receives link:
zerotrace.com/msg/uuid-123 - Sees a “Secure Data Packet Preview”
- Must authenticate through Twitter OAuth
-
Validation step: ```python authenticated_user.id == target_user.id
If matched → decrypt and reveal
If not → ACCESS DENIED (Red Screen of Death)
3. The Purge (Self-Destruct)
-
When message renders, is_read = True
-
A 60-second countdown starts in the browser
-
Reloading or revisiting the link = rejected forever
| Layer | Technology |
|---|---|
| Backend | Python / Django 5 |
| Security | cryptography (Fernet) |
| Authentication | Twitter API v2 (tweepy) |
| Frontend | HTML5 + CSS3 (CRT Scanlines, Glitch FX, Web Audio API) |
| Database | PostgreSQL (Prod) / SQLite (Dev) |
The “Burn” Logic
@login_required
def message_view(request, tweet_uuid):
tweet = get_object_or_404(Tweet, uuid=tweet_uuid)
# 1. THE KILL SWITCH
if tweet.is_read:
return render(request, 'error.html', {'msg': 'CONNECTION TERMINATED: Data Purged.'})
# 2. IDENTITY VERIFICATION
if tweet.username.lower() != request.user.username.lower():
return render(request, 'error.html', {'msg': 'ACCESS DENIED: Biometrics Mismatch.'})
# 3. DECRYPT & BURN
try:
f = Fernet(tweet.key.encode())
payload = f.decrypt(tweet.message.encrypted_text.encode()).decode()
tweet.is_read = True # link dies immediately
tweet.save()
return render(request, 'terminal.html', {'payload': payload})
except:
return render(request, 'error.html', {'msg': 'Decryption Error.'})
Why I Built This
We’re moving toward a walled-garden internet. As AI spam increases, high-value individuals will only build higher walls.
ZeroTrace is my attempt to build a ladder.
It forces the sender to put effort into communication — acting as a natural spam filter. If someone sends you a ZeroTrace uplink, you know it isn’t a mass-marketing blast. It’s a private, encrypted payload meant for your eyes only.